Mobile device forensics
Official technological partner of Oxygen Forensics
Over the last decades, there has been a growing number of smartphone users. These mobile devices save most of the data and information of their users, which enables us to have insight into the list of calls they made, the appointments they arranged, and the people they have had contact with. Moreover, there is a possibility of data recovery and extraction.
Regarding this issue, Mobile device forensics became the inevitable part in a various number of investigations, ranging from the private to the corporate and criminal ones. There is a growing recognition that most of the data once saved on the mobile devices can be found, extracted, and analysed; the saved electronic codes often represent the key, indisputable evidence of a certain activity, malpractice, or criminal act.
Recover Deleted Data
In order for a mobile device forensic analysis to be complete, it is necessary to make a physical extraction, that is, to extract the data. Physical extraction provides a bit-by-bit copy of the entire flash memory of a mobile device. This extraction method not only enables the acquisition of intact data, but also data that is hidden or has been deleted.
Important: We can retrieve deleted messages or datas ONLY IF there were nor overwritten by other Datas on the phone memory during the regular use.
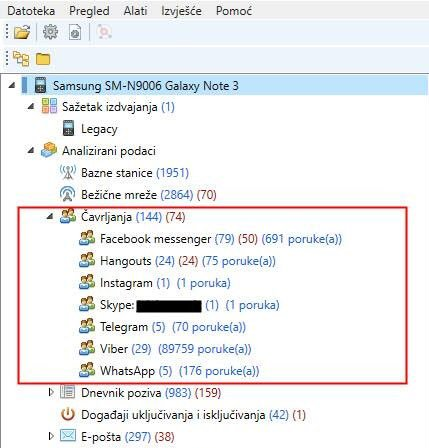
Links and Stats
Links and Stats section provides a convenient tool to explore social connections between device users by analyzing calls, text, multimedia and e-mail messages and Skype activities. Diagram view with a graphical chart presents a quick overlook of communication circles, allowing forensic experts to determine and analyze suspects’ communications with all details at a glance.
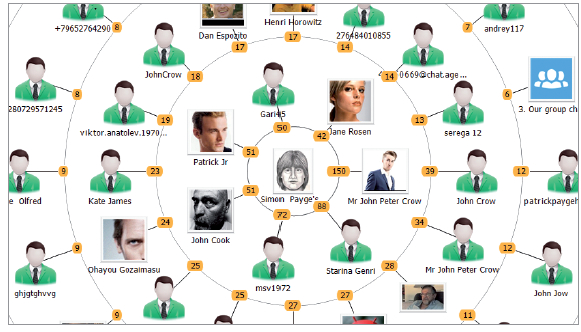
Cloud Data Extraction
Oxygen Forensic® Cloud Extractor acquires data from more than 20 cloud storages: iCloud contacts and calendar, Google Drive, Google Location History, Live contacts and calendar, OneDrive, Dropbox and Box as well as from a wide range of social media including Twitter and Instagram. Forensic experts may utilize credentials and tokens extracted from the mobile device to enter the cloud account.
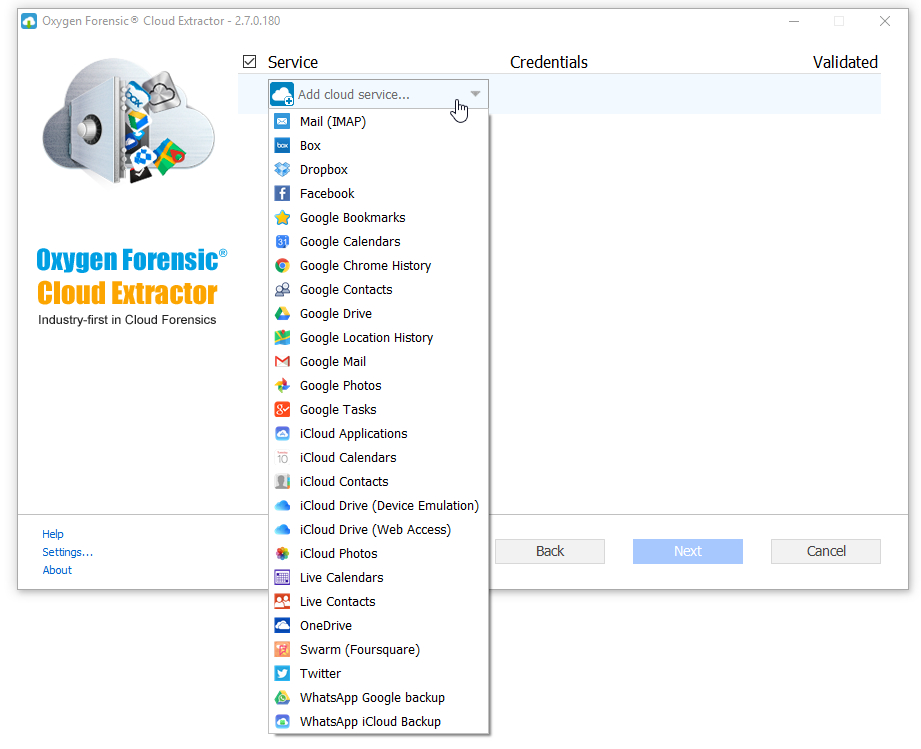
Spyware detection
With the spyware detection system we are able to detect the infected apps on you mobile devices, as well as to analyze their security logs and configuration files. Through such an analysis, forensic investigator can acquire information and access to some additional information such as configuration, user names, GPS Loggers with coordinates and date, to name but a few.
Video: Oxygen Forensic Detective - Spyware detection
Video: Cellebrite UFED Physical Analyzer - Spyware detection
WARNING: If you suspect that your mobile phone is being tracked or monitored, turn it off, or set the airplane mode. In case you call us from the infected phone and ask for help, the intruder may remove the malware app with the remote control.
User Lock Code Recovery Tool
Lock Code Recovery Tool provides solutions for locked devices. The tool supports Android and iOS operating systems, and enables users to access a locked device to reveal the device’s user lock code on-screen.
Video: Cellebrite UFED 4PC - Bypassing the passcode.

We use cutting-edge technology
We are the only agency in Croatia, as well as in the overall region, which uses the Oxygen Forensics® and Cellebrite's UFED forensic technology for mobile devices, widespread among different governmental organisations, as well as the law enforcement agencies in over 100 countries worldwide, such as FBI or DEA, US Army, US Department of Defense (DOD), US Department of Justice, US Department of Homeland Security, Interpol, London Metropolitan Police, French National Police and Gendarmerie, German Federal Criminal Police Office, Italian Financial Guard, Spanish Civil Guard, and many others. This cutting edge technology enables physical extraction, decoding, analysis and reporting of data from the widest range of mobile phones, portable GPS devices, tablets, memory cards and phones manufactured with Chinese chipsets.

Video: Cellebrite UFED 4PC
Advanced forensic methods
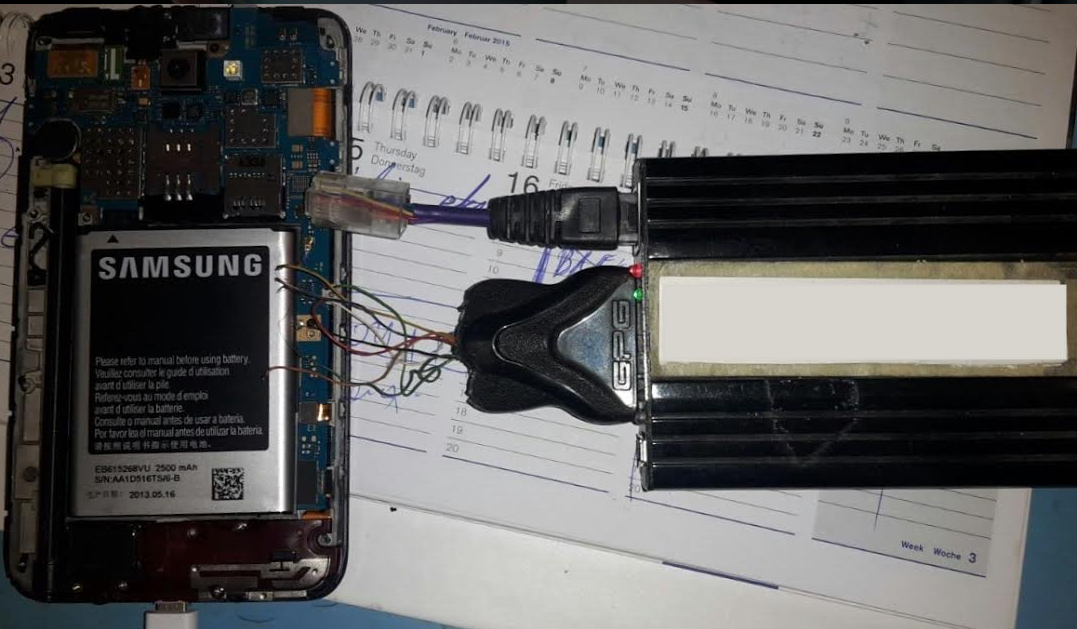
JTAG Forensics
This non-destructive method of extracting all data from a device is the next option when traditional forensic methods fail. JTAG is viable when a device is password/pattern lock protected, a data port is unavailable, or even if the device is physically damaged or partially destroyed. This specialized service is remarkably affordable and appropriate for use by a variety of entities including law enforcement, attorneys, private individuals, and institutions.
Chip-Off Forensics
Chip-Off Forensics--or forensic desoldering--is effective but destructive and therefore is usually the last option when it comes to extracting data from devices. This method involves a special process and equipment to remove memory chips and extract the stored data for analysis. The end result is that the device is destroyed, but the data is preserved in a forensically-sound manner.












